Series: Kubernetes at home
- Kubernetes at home - Part 1: The hardware - January 02, 2021
- Kubernetes at home - Part 2: The install - January 05, 2021
- Kubernetes at home - Part 3: HAProxy Ingress - January 05, 2021
- Kubernetes at home - Part 4: DNS and a certificate with HAProxy Ingress - January 07, 2021
- Kubernetes at home - Part 5: Keycloak for authentication - January 16, 2021
Kubernetes at home - Part 6: Keycloak authentication and Azure Active Directory - January 17, 2021
- Kubernetes at home - Part 7: Grafana, Prometheus, and the beginnings of monitoring - January 26, 2021
- Kubernetes at home - Part 8: MinIO initialization - March 01, 2021
- Kubernetes at home - Part 9: Minecraft World0 - April 24, 2021
- Kubernetes at home - Part 10: Wiping the drives - May 09, 2021
- Kubernetes at home - Part 11: Trying Harvester and Rancher on the bare metal server - May 29, 2021
- Kubernetes at home - Part 12: Proxmox at home - December 23, 2021
Kubernetes at home - Part 6: Keycloak authentication and Azure Active Directory
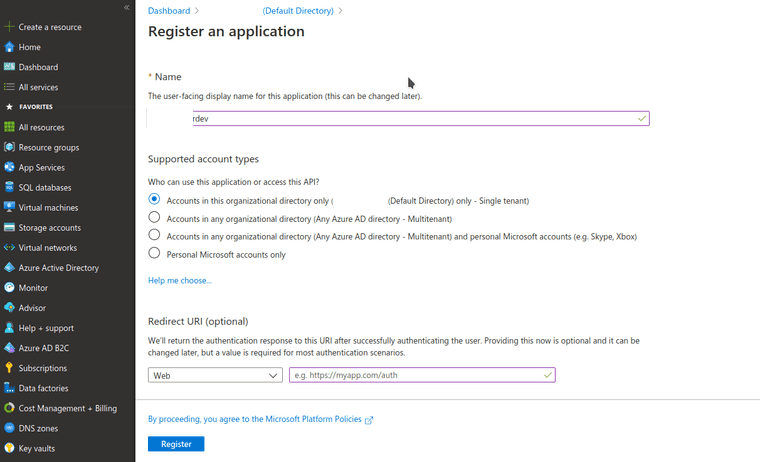
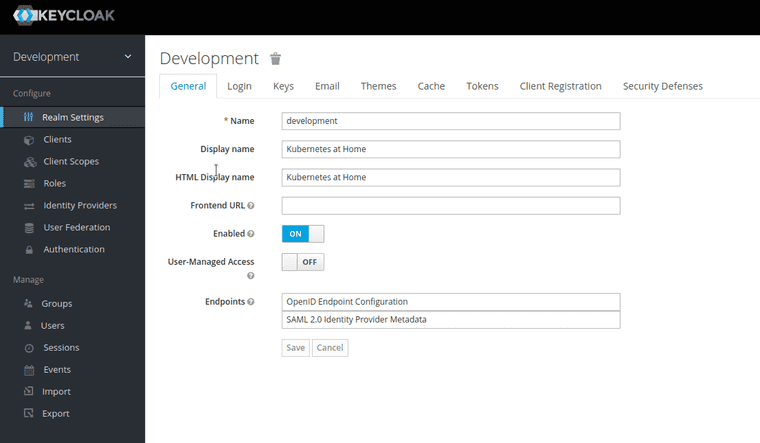
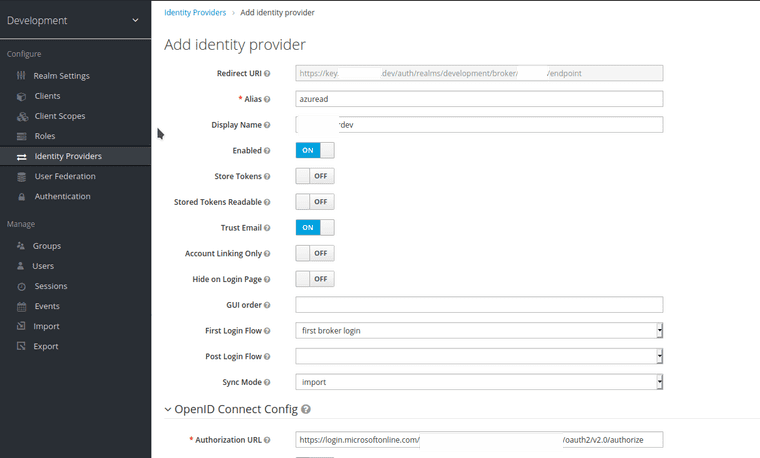
Here’s a quick detour into adding Azure Active Directory as an Identity Provider for Keycloak in my home Kubernetes single-node cluster. I’m not going into much detail since OpenID Connect is so well documented. Most of the steps for this specific connection can also be found here.
High level steps
- Registering new application in Azure
- Registering new realm in Keycloak, so I’m not using the main one.
- Registering new identity provider in Keycloak. Most of the OpenID Connect config can be automatically imported from the OpenID well-known configuration.
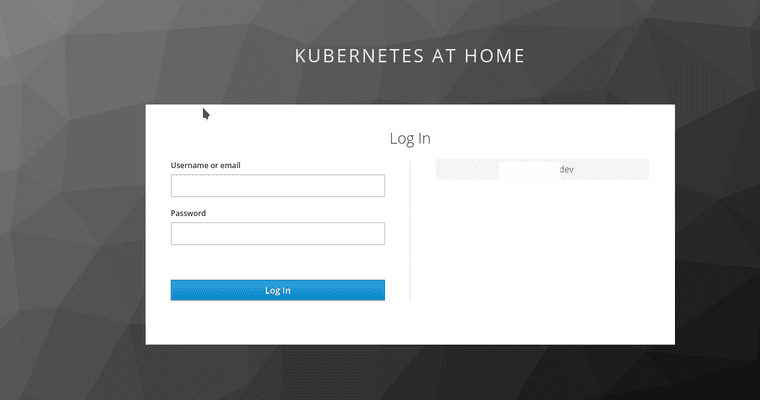
- Keycloak has a small client already built-in for user account management, and that provides a handy method to test using the new identity provider.
- So long as you can login to Azure Active Directory, you can go ahead and get into Keycloak.
Summary and motivation
For the most part, I want to be able to have a self-sufficient Kubernetes cluster at home; however, this is a happy medium in my mind.
By using Azure AD as an identity provider, I get some convenience that is optional. THe entirety of the identity provider could be inaccessible or removed, and I’d still have control of users and configuration here. Further, in a theoretical world where I start shipping software from this local environment, authentication is a cross-cutting concern that I’d happily replace with a cloud service once this all left my home network.
Series: Kubernetes at home
- Kubernetes at home - Part 1: The hardware - January 02, 2021
- Kubernetes at home - Part 2: The install - January 05, 2021
- Kubernetes at home - Part 3: HAProxy Ingress - January 05, 2021
- Kubernetes at home - Part 4: DNS and a certificate with HAProxy Ingress - January 07, 2021
- Kubernetes at home - Part 5: Keycloak for authentication - January 16, 2021
Kubernetes at home - Part 6: Keycloak authentication and Azure Active Directory - January 17, 2021
- Kubernetes at home - Part 7: Grafana, Prometheus, and the beginnings of monitoring - January 26, 2021
- Kubernetes at home - Part 8: MinIO initialization - March 01, 2021
- Kubernetes at home - Part 9: Minecraft World0 - April 24, 2021
- Kubernetes at home - Part 10: Wiping the drives - May 09, 2021
- Kubernetes at home - Part 11: Trying Harvester and Rancher on the bare metal server - May 29, 2021
- Kubernetes at home - Part 12: Proxmox at home - December 23, 2021